views
The world's mobile phone carriers have failed to implement technology fixes available since 2008 that would have thwarted the National Security Agency's ability to eavesdrop on many mobile phone calls, a cyber security expert says.
Karsten Nohl, chief scientist with Berlin's Security Research Labs, told Reuters ahead of a highly anticipated talk at a conference in Germany that his firm discovered the issue while reviewing security measures implemented by mobile operators around the world.
Nohl also told Reuters that the carriers had failed to fully address vulnerabilities that would allow hackers to clone and remotely gain control of certain SIM cards. Those vulnerabilities were pointed out in July.
While the German cryptologist criticised carriers for failing to implement technology to protect customers from surveillance as well as fraud, he said he does not think they did so under pressure from spy agencies.
"I couldn't imagine it is complicity. I think it is negligence," he said. "I don't want to believe in a worldwide conspiracy across all worldwide network operators. I think it is individual laziness and priority on network speed and network coverage and not security."
A spokeswoman for the GSM Association, which represents about 800 mobile operators worldwide, said she could not comment on Nohl's criticism before seeing his presentation on the topic at the Chaos Communications Congress in Hamburg, Europe's biggest annual conference on hacking, security and privacy issues.
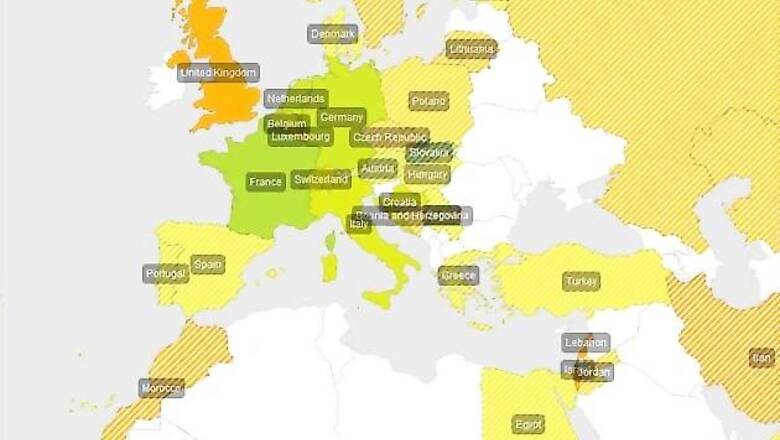
Nohl uncovered the issue while working on a project known as the GSM Security Map, which evaluates security of mobile operators around the globe. The map, which can be found at www.gsmmap.org, is partially funded with a grant from the US government's Open Technology Fund, according to Nohl.
None of the carriers surveyed had implemented measures for thwarting a method that allows the NSA to eavesdrop on most mobile calls by unscrambling a widely used encryption technology known as A5/1, Nohl said.
The Washington Post reported on December 13 that documents leaked by former NSA contractor Edward Snowden showed the agency can crack A5/1. Nohl said that method would have been blocked if carriers had applied two patches released in 2008.
Nohl is credited with leading research teams that have uncovered major flaws in mobile technology in recent years.
In July, he reported on security vulnerabilities that would allow hackers to gain remote control of and clone certain mobile SIM cards. The unprecedented work prompted a United Nations group known as the International Telecommunications Union, which advises nations on cyber security plans, to urge the industry to take quick action to tackle the vulnerabilities.
Once a hacker copies a SIM, it can be used to make calls and send text messages impersonating the owner of the phone, said Nohl, who has a doctorate in computer engineering from the University of Virginia.
A few weeks after Nohl disclosed his findings, he said it looked like most carriers had implemented fixes to prevent such attacks.
Yet he said on Friday that while conducting research for the GSM Security Map project, he learned on closer inspection that those fixes still left plenty of room for attacks, making customers on many networks vulnerable.
"I need to go back on what I said. The majority of the operators only addressed the symptoms, not the root cause," Nohl said.
He said that his firm launched the GSM Security Map project to pressure mobile operators around the world to boost security. The effort will also push researchers like himself not to be complacent.
"We as researchers must not give up so easily like we did in July, when we said 'The network operators addressed it. We are so proud. We changed the world,'" Nohl said.
The group will continue to update the map, which has detailed reports for each country surveyed that describe security of individual carriers.
In the map's initial release on Friday, the country whose networks were rated the most secure was France.
Not all countries are surveyed, however, because the group does not yet have enough data.
####



















Comments
0 comment