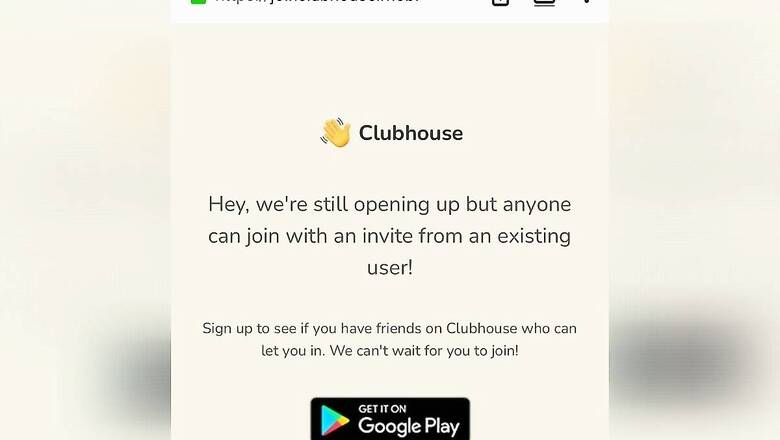
views
Clubhouse, the audio-based chat platform, has gained massive popularity in the last few weeks, but sadly, the application is currently limited to iOS devices. Though the company has announced its plans to expand Clubhouse to Android smartphones, the availability details remain unclear. However, ahead of the official launch, an imposter Clubhouse app for Android has appeared on the internet containing a trojan – nicknamed “BlackRock.” The malware spotted by Ireland-based ESET researcher Lukas Stefanko seemingly gains unauthorised login credentials from more than 450 apps and can bypass SMS-based two-factor authentication. In a blog post, the researcher adds that the “malicious package” is served from a website that has the look and feel of the genuine Clubhouse website. The website essentially allows users to download the Android Package Kit or APK file.
The imposter Clubhouse for Android target list includes well-known financial and shopping apps, cryptocurrency exchanges, and social media platforms. For starters, Twitter, WhatsApp, Facebook, Amazon, Netflix, Outlook, eBay, Coinbase, Plus500, Cash App, BBVA and Lloyds Bank are all on the list, ESET notes. In other words, as soon as the user launches one of the targeted applications, the BlackRock malware will create a “data-stealing overlay of the application and request the user to log in.” In this case, the user hands over their credentials to the cybercriminals instead of logging in. The security firm adds that SMS-based two-factor authentication (2FA) to help prevent anyone from infiltrating accounts would not help in this case since the BlackRock malware can also intercept text messages.
Malicious web claiming to offer #Clubhouse for Android spreads banking trojan Blackrock. It lures credentials from 458 apps – financial, cryptocurrency exchanges & wallets, social, IM and shopping apps. There is currently no official Clubhouse app for Android. #ESETresearch 1/2 pic.twitter.com/azlxjvIgNO— ESET research (@ESETresearch) March 16, 2021
However, users (especially Android smartphone users) can still notice signs of the app being fishy through the website despite featuring the same design as the original website. The URL, for instance, uses “.mobi” top-level domain (TLD) rather than “.com.” Moreover, clicking on ‘Get in on Google Play’ automatically downloads the file instead of redirecting it to the app page. “By contrast, legitimate websites would always redirect the user to Google Play, rather than directly download an Android Package Kit or APK for short,” said security researcher Stefanko. The cybersecurity firm adds that users must use only the official stores to download apps to their devices to ensure online security. Also, they should be wary of what kinds of permissions applications seek.
Read all the Latest News, Breaking News and Coronavirus News here




















Comments
0 comment