
views
Cybersecurity watchdog Sophos Labs has published the detailed rise, spread, workings and intermediate disappearance of a particularly enigmatic piece of malware, dubbed Baldr. In a 72-page report that elaborately logs the trojan tool, Baldr is primarily referenced as a malware that began spreading through gaming communities, before proceeding to affect a wide range of devices and steal data including personal identification, information caches, financial data and more. At its best, Baldr can be described as a malware that was stitched together from numerous other families of malicious tools, thereby being described by Sophos threat researcher Albert Zsigovits as the "Frankenstein's monster of malware".
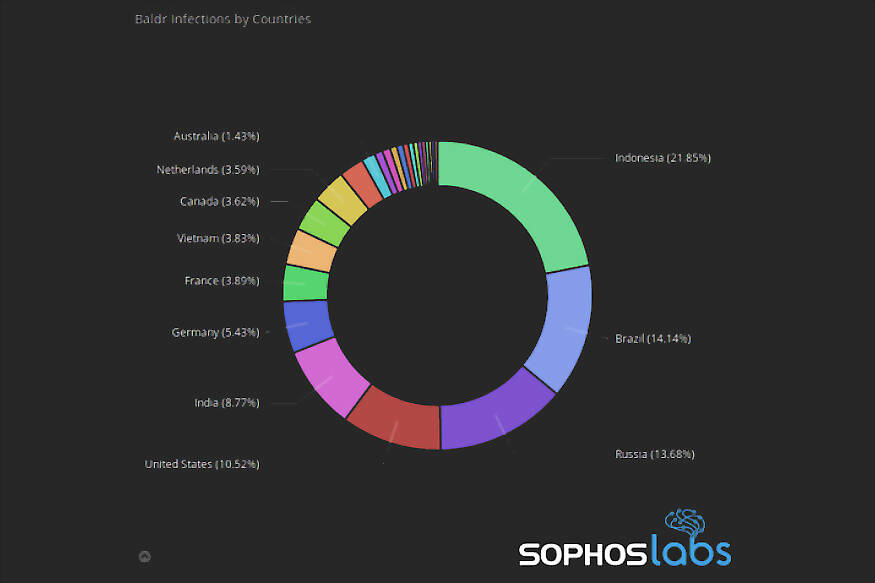
The far-reaching effects of Baldr spread to India as well, which accounted for 8.77 percent of Baldr's overall infected devices database. To get a grasp of Baldr's reach, the first point to consider are sources that were used to spread it. These seemingly include YouTube, Sony, Battle.net, Steam and Epic, as well as messaging channels on encrypted communication services such as Discord and Telegram. Each of these media are immensenly popular in the gaming community, particularly in the PC gaming circuit where the device of browsing is often the very same machine used as primary by the gamer. Baldr, in this case, was distributed from the dark web by a primary distributor working closely with its creator, who released the malware for sale on deepweb, a section of the internet that is slightly less difficult to access.
The distribution channels then spread the malware through links that offered cheats and level hacks on popular gaming titles such as Counterstrike: Global Offensive and Apex Legends, each of which have massive gamer bases. Over time, Zsigovits of Sophos estimates that malware sales alone have raked up revenues of up to $30,000 (~Rs 20,00,000). While this might seem paltry in the malware scheme of things, Baldr is believed to have primarily been a password-stealing tool, which has also collected plenty of sell-worthy information such as credit card details, government-issued IDs and more. Add this possible revenue to Baldr's worth, and it immediately has the potential to shoot into the millions.
Baldr also affected cryptocurrency wallets in order to steal data, which has the reverse effect of protecting it thanks to blockchain's benefits. Over time, the Baldr tool has been evolved to become more mature in nature, with later variants featuring the coveted self-destruct ability — leaving barely any trace in affected machines of what happened. It also employed tactics such as strategic algorithmic pauses, which would trick security sandboxes to read it as a break in the operations, hence losing track and not discovering the point of origin.
Given how Baldr could be adapted into different forms and hence service different purposes, the security threats that could rise out of Baldr are numerous. Zsigovits states, "As its distribution increases, so do the variety of methods that Baldr customers use to infect customers, including the use of maliciously crafted .ace archives and Office documents, which are either hosted for download or emailed to victims." However, Zsigovits and his team also noticed an unnatural hiatus that the malware seems to have taken, although that does not mean that its run is over. As Zsigovits states, "The main developer and the principal distributor seem to have had a (somewhat public) falling out, with the distributor dropping Baldr as a product for sale. But the malware has not ceased functioning, and we expect it to re-emerge, possibly with a new name."
The last message, posted by Baldr's dark web distributor, reads, "Product support is stopped by the project coder at the moment BALDR will no longer be updated. Work for old customers is unlimited, but the product will not be cleaned/maintained/updated anymore. Look for a replacement product." This leaves open the existing possibilities of Baldr and the threats that tools derived from it can present, and Sophos Labs maintains that any user should consistently update their software to remain as safe as possible. As of now, the million-dollar trojan may be off the table for attackers, but given the way cybercrime works, a return for the tool can occur any moment, and in any form.


















Comments
0 comment